Tuesday, October 11, 2011
Wednesday, September 28, 2011
DSget
Monday, September 26, 2011
Memory Monitoring
Processes section
Click Start, click in the Start Search box, type resmon.exe, and then press ENTER.
To pause data collection and review the current data, click Monitor, and then click Stop Monitoring. When you are ready to begin collecting data again, click Monitor, and then click Start Monitoring.
The Memory tab’s Processes section displays key metrics related to how the system’s processes use memory. Here’s information about the metrics:
- Image. Process executable file name. This is the name of the process that is actively using the disk.
- PID. Process ID. This is the ID number associated with the process; it is useful if you want to use other utilities to manage processes, or if you want to easily match up processes with Task Manager.
- Hard Faults/sec. A hard fault doesn’t necessarily indicate a critical error condition, though it may indicate that the server is in need of more RAM. A hard fault occurs every time the system uses the swap file on the disk. This is important because disk storage is much, much slower than RAM, so each time the system uses disk-based virtual RAM, there is a significant performance penalty. If you see hard faults on a regular basis (especially if the numbers are large), you should consider adding more RAM to the server. Hard faults are sometimes referred to as Page Faults.
- Commit (KB). This is the total amount of physical and virtual memory (page file) that is committed to this specific process.
- Working Set (KB). This is the amount of physical memory that is committed to this particular process. This number should be the total of the next two metrics, which are its components.
- Shareable (KB). This is the total amount of physical memory that is committed to this particular process but that can also be shared with another process.
- Private (KB). This is the total amount of physical memory that is committed to this particular process but cannot be shared with another process.
Physical Memory
Below the Processes section, you’ll see a section called Physical Memory that contains this information:
- In Use. The amount of memory that is in use right now.
- Available. Of the total physical memory in the system, this is how much is still available for allocation.
- Hardware Reserved. This identifies the amount of memory that various hardware devices have set aside for their dedicated use. Almost any device in the server can add to this metric. This Exchange Server clocks in at 1MB.
- Modified. As information is written into memory pages, it stays there while other processing goes on behind the scenes. As information is updated on these memory pages, those pages are marked as having been modified. After a period of time, in order to ensure that the system makes the best use of available memory resources, modified pages that have not been accessed in a while might be moved to the standby category.
- Standby. This memory contains cached data and code that is not actively in use but that may be called into action at some point. Windows manages this class of RAM by prioritizing each page that comes in. As other processes need RAM, low priority pages from this pool are reallocated to other needs.
- Free. This value is how much RAM is currently available above and beyond what is in use. You might think that having such a small amount of RAM marked as free in this 16 GB system might identify a major problem, but that’s the case. With many of Microsoft’s newer products, it’s better to use as much RAM as possible than to leave it idle. Products such as Exchange use RAM to its fullest extent and cache portions of the product for faster access.
One common mistake it to use the “In Use” and “Available” metrics as the sole indicators for overall system health and to get concerned when particular processes appear to be eating too much RAM. This is why you need to understand how the application is supposed to behave.
For example, Exchange 2010 often uses as much memory as you can throw at it; this is by design. The thinking is that Exchange will use RAM to cache as much information as possible in order to improve overall performance. So it’s important to look at other metrics, such as Hard Faults, to determine if there is a really a RAM-related performance issue on an Exchange 2010 machine. If a service shouldn’t be using a lot of RAM and it is, you need to do more troubleshooting; this is the point at which you might fire up Performance Monitor to gather more specific details.
Source: Click here
Sunday, September 25, 2011
Net Time Commands
| Net Time options | Description |
| Net Time | Displays the time of your time server |
| Net Time \\computername | Displays the computer name time |
| Net Time /DOMAIN:domainname | Displays the time on a DC domain name |
| Net Time /domain/set | Sets computer time to match time on Domain Controller |
| Net Time /RTSDOMAIN:domainname | Displays the time on a time server in the domain name |
| Net Time /querysntp | Displays the SNTP source for the time server |
| Net Time /setsntp:ntpserver | Sets the SNTP source for the time server |
| Net Time /setsntp | Clears the SNTP source for the time server |
Net Time Commands
| Net Time options | Description |
| Net Time | Displays the time of your time server |
| Net Time \\computername | Displays the computer name time |
| Net Time /DOMAIN:domainname | Displays the time on a DC domain name |
| Net Time /domain/set | Sets computer time to match time on Domain Controller |
| Net Time /RTSDOMAIN:domainname | Displays the time on a time server in the domain name |
| Net Time /querysntp | Displays the SNTP source for the time server |
| Net Time /setsntp:ntpserver | Sets the SNTP source for the time server |
| Net Time /setsntp | Clears the SNTP source for the time server |
Thursday, September 22, 2011
Run Control Panel Applets as Another User
| Control Panel Applet | Filename |
| Accessibility | access.cpl |
| Add New Hardware | hdwwiz.cpl |
| Add/Remove Programs | appwiz.cpl |
| Date/Time Properties | timedate.cpl |
| Display Properties | desk.cpl |
| FindFast | findfast.cpl |
| Internet Properties | inetcpl.cpl |
| Joystick Properties | joy.cpl |
| Keyboard Properties | main.cpl |
| Local Users management | nusrmgr.cpl |
| Microsoft Exchange | mlcfg32.cpl |
| Microsoft Mail Post Office | wgpocpl.cpl |
| Modem Properties | modem.cplNote: In Windows NT 4.0, W2K, XP and Windows 2003 - Modem properties is telephon.cpl |
| Mouse Properties | main.cpl |
| Multimedia Properties | mmsys.cpl |
| Network Properties | netcpl.cplNote: In Windows NT 4.0, W2K, XP and Windows 2003 - Network properties is Ncpa.cpl |
| Password Properties | password.cpl |
| Power Options | powercfg.cpl |
| Regional Settings | intl.cpl |
| Sound Properties | mmsys.cpl |
| System Properties | sysdm.cpl |
Tuesday, September 20, 2011
Command AD Queries
Find all users whose email address contains …
(objectClass=user)(mail=*@afl.maori.nz)
http://www.petri.co.il/ldap_search_samples_for_windows_2003_and_exchange.htm
Basic LDAP Syntax
• = (EQUAL TO)
This LDAP argument means a certain attribute must be equal to a certain value to be true. For example, if you want to find all objects that have the first name of John, you would use:
Copy Code
(givenName=John)
This would return all objects that have the first name of John. Parentheses are included to emphasize the beginning and end of the LDAP statement.
• & (logical AND)
You use this syntax when you have more than one condition, and you want all conditions in the series to be true. For example, if you want to find all of the people that have the first name of John and live in Dallas, you would use:
Copy Code
(&(givenName=John)(l=Dallas))
Notice that each argument is in its own set of parentheses. The entire LDAP statement must be encompassed in a main set of parentheses. The & operator means that each argument must be true for this filter to apply to your object in question.
• ! (logical NOT)
This operator is used to exclude objects that have a certain attribute. Suppose you need to find all objects except those that have the first name of John. You would use the following statement:
Copy Code
(!givenName=John)
This statement would find all objects that do not have the first name of John. Notice that the ! operator goes directly in front of the argument and inside the argument's set of parentheses. Because there is only one argument in this statement, it is surrounded with parentheses for illustration.
• * (wildcard)
You use the wildcard operator to represent a value that could be equal to anything. One such situation might be if you wanted to find all objects that have a value for title. You would then use:
Copy Code
(title=*)
This would return all objects that have the title attribute populated with a value. Another example might be if you know an object's first name starts with Jo. Then, you could use the following to find those:
Copy Code
(givenName=Jo*)
This would apply to all objects whose first name starts with Jo.
• The following are more advanced examples of LDAP syntax:
• You need a filter to find all objects that are in Dallas or Austin, and that have the first name of John. This would be:
Copy Code
(&(givenName=John)(|(l=Dallas)(l=Austin)))
• You have received 9,548 events in the Application log, and you need to find all of the objects that are causing this logging event. In this case, you need to find all of the disabled users (msExchUserAccountControl=2) that do not have a value for msExchMasterAccountSID. This would be:
Copy Code
(&(msExchUserAccountControl=2)(!msExchMasterAccountSID=*))
• Note:
The ! operator in conjunction with the wildcard operator will look for objects where that attribute is not set to anything.
Check server last reboot time
NK 2 File Location
The location of the NK2 file of Outlook
The location of the NK2 AutoCompelete file created by Outlook might be different from one computer to another, depending on the operating system and the version of Outlook.
Here's the rules for finding the location of your NK2 file:
- For Outlook 2003/2007 with Windows 2000, Windows XP, or Windows Server 2003:
The location of the nk2 file is C:\Documents and Settings\[User Profile]\Application Data\Microsoft\Outlook
The name of the NK2 file is identical to the Outlook profile name, with .nk2 extension. - For Outlook 2003/2007 with Windows Vista, Windows 7, or Windows server 2008:
The location of the nk2 file is C:\Users\[User Profile]\AppData\Roaming\Microsoft\Outlook
The name of the NK2 file is identical to the Outlook profile name, with .nk2 extension. - For Outlook 2010 with Windows Vista, Windows 7, or Windows server 2008:
The nk2 file is located in C:\Users\[User Profile]\AppData\Local\Microsoft\Outlook\RoamCache
The name of the NK2 file is in the following format: Stream_Autocomplete_X_AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.dat The X is the file index (usually 0) and AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA is a random 16-byte key in hexadecimal format. - For Outlook 2010 with Windows XP:
The nk2 file is located in C:\Documents and Settings\[User Profile]\Local Settings\Application Data\Microsoft\Outlook\RoamCache
The name of the NK2 file is in the following format: Stream_Autocomplete_X_AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA.dat The X is the file index (usually 0) and AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA is a random 16-byte key in hexadecimal format.
Commands to find out the CAS Server on Exchange
Tuesday, September 6, 2011
Domain Local vs Global Groups
Members of Global Group can come only from local domain but members can access resources in any domain.
Domain Local Group:
Members of Local Group can come from any domain but members can access resources only in local domain.
Universal Group:
Members can come from any domain and members can access resource in any domain.
Monday, September 5, 2011
Deleting Registry Keys and Values
To delete a registry key with a .reg file, put a hyphen (-) in front of the RegistryPath in the .reg file. For example, to delete the Test subkey from the following registry key:
HKEY_LOCAL_MACHINE\Software
put a hyphen in front of the following registry key in the .reg file:
HKEY_LOCAL_MACHINE\Software\Test
The following example has a .reg file that can perform this task.
[-HKEY_LOCAL_MACHINE\Software\Test]
To delete a registry value with a .reg file, put a hyphen (-) after the equals sign following the DataItemName in the .reg file. For example, to delete the TestValue registry value from the following registry key:
HKEY_LOCAL_MACHINE\Software\Test
put a hyphen after the "TestValue"= in the .reg file. The following example has a .reg file that can perform this task.
HKEY_LOCAL_MACHINE\Software\Test
"TestValue"=-
To create the .reg file, use Regedit.exe to export the registry key that you want to delete, and then use Notepad to edit the .reg file and insert the hyphen.
1) Right Click on the Registry Folder and select export;
2) Replace the registry value with -
See example as per below.

Sunday, September 4, 2011
Fix Temporary Profile in Windows 7 Issue
1)Log in with temp profile.
2)Start registry editor by typing regedit in find box in Windows 7.
3)Navigate the following location in Windows 7.
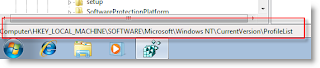
4)You can see similar keys under profile list with .bak difference, as shown below.
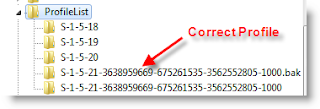
5)You correct profile key is marked as bak. Currently your Windows 7 computer logged in with fresh profile with same key. So, rename the new profile key ( which is not having.bak) and remove .bak from correct profile key. See below.
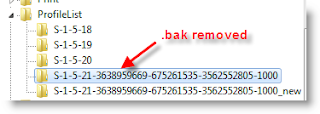
6)That’s it. Log off and log in with your user name and password. You must get your icons and profile settings back in Windows 7. This is very simple and easy method to fix temp profile in Windows 7 issue.
Get the email addresses for all users in a security group
dsquery group -name "VDI_View_Local_Mode_Pool_L3B1P1" | dsget group -members | dsget user -email > c:\Queries\Local_Mode.txt
dsquery group -name "VDI_View_MS_Users_Floating_Pool_C1B1P1" | dsget group -members | dsget user -email > c:\Queries\MS_Floating_Pool.txt
dsquery group -name "VDI_View_Floating_Pool_C1B1P1" | dsget group -members | dsget user -email > c:\Queries\Floating_Pool.txt
dsquery group -name "VDI_View_Dedicated_Pool_C2B1P1" | dsget group -members | dsget user -email > c:\Queries\Dedicated_Pool.txt
Monday, August 15, 2011
Check System Uptime
net statistics workstation | find "Statistics since"
systeminfo
systeminfo| find "System Boot Time"
Wednesday, August 3, 2011
AD Query

Locked Out Users - Displays all the user accounts that are locked out
(&(&(&(&(objectCategory=person)(objectClass=user)(lockoutTime:1.2.840.113556.1.4.804:=4294967295)))))
Dial In Access - Displays all the user accounts with Dial In Access
(&(&(&(&(objectCategory=person)(objectClass=user)(msNPAllowDialin=TRUE)))))
Disabled User Accounts - Displays all the user accounts that are currently disabled
(&(objectCategory=person)(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=2))
Non Expiring Accounts - Displays all the user accounts that are set to not expire
(&(objectCategory=person)(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=65536))
Active Accounts - Displays all the users account that are active
(&(&(objectCategory=person)(objectClass=user)(!userAccountControl:1.2.840.113556.1.4.803:=2)))
Hidden Mailboxes - Displays all accounts with hidden Mailboxes
(&(objectCategory=person)(objectClass=user)(msExchHideFromAddressLists=TRUE))
Windows XP Computers - Displays all computers running Windows XP
(&(&(&(&(&(&(&(objectCategory=Computer)(operatingSystem=Windows XP Professional)(operatingSystemServicePack=Service Pack 3))))))))
Vista Machines – Displays all computers running Windows Vista
(&(&(&(&(&(&(sAMAccountType=805306369)(objectCategory=computer)(operatingSystem=Windows Vista*)))))))
Vista Machines – SP1
(&(&(&(&(sAMAccountType=805306369)(objectCategory=computer)(operatingSystem=Windows Vista*)(operatingSystemServicePack=Service Pack 1)))))
All Computers - Displays all computers
(sAMAccountType=805306369)
Windows Server 2000 - Displays all computers running Windows Server 2000 (not including DC’s)
(&(&(&(&(&(objectCategory=Computer)(operatingSystem=Windows 2000 Professional))))))
Windows Server 2003 - Displays all computers running Windows Server 2003 (not including DC's)
(&(&(&(samAccountType=805306369)(primaryGroupID=516)(objectCategory=computer)(operatingSystem=Windows Server 2003*))))
Windows Server 2008 - Displays all computers running Windows Server 2008 (not including DC's)
(&(&(&(&(samAccountType=805306369)(!(primaryGroupId=516)))(objectCategory=computer)(operatingSystem=Windows Server 2008*))))
All Windows Server Domain Controllers - Displays all computers that are Domain Controllers
(&(&(&(sAMAccountType=805306369)(useraccountcontrol:1.2.840.113556.1.4.804:=67117056))))
My Document Folder Redirection
Check in these two places
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Friday, June 17, 2011
VMware vSphere 4 ( ESXi 4) on Windows 7 PC by VMware Workstation 7
Basic Requirements for VMware vSphere 4( ESXi 4) on a PC
1) Minimum 2GB RAM should be allocated for ESXi 4 virtual machine. So, you must have minimum 3GB RAM on computer.
2) Hardware virtualization should be available and enabled on motherboard.
How to Confirm Virtualization Technology is Enabled or Disabled?
1) If your processor is Intel, then you can use this free utility to confirm the result which operating system is sensing.
Download Intel tool to confirm virtualization technology
The result of this utility brings a screen as shown below,
2) For AMD Processors download the below utility.
3) Microsoft Tool to check hardware virtualization Technology ( VT)
Download the free tool from Microsoft here.
Source:
http://www.sysprobs.com/vmware-vsphere-4-esxi-4-windows-7-vmware-workstation-7-pc
http://www.sysprobs.com/disable-enable-virtualization-technology-bios
How to install VMware VSphere ESXi 4 on a desktop PC
Trying to figure out how to install VMWare Vsphere ESXi 4.0 on a home desktop computer but now sure how? Neither was I but I finally figured it out and I’ll tell you how!
Over the last year, I’ve been getting very involved in VMware ESX installations and rollouts at work. It started with doing several hundred P2V’s (physical machine to virtual machine conversions) then onto the server side and actually configuring the servers. We started with ESX 3.5 then upgraded to ESXi 4.0 which is now known as VSphere.
I took a couple of VMware training classes and realized that there was a lot of capabilites in VSphere that we weren’t using at my company. Unfortunately, since it was a production environment, tinkering and experimenting on the ESX clusters at the office wasn’t an option. I’m the type of person that when I get into a technology, I want to know as much about it as possible. It also helps to learn as much as possible as it makes you more valuable at work and to potential (higher paying) employers.
RESEARCH
My research began to find out what it would take to build a VMware VSphere ESXi 4.0 server at home.
A quick google search showed it was very possible to build a home ESX server, but unlike Windows servers there were very specific hardware requirements. Even tougher, VMware doesn’t list what desktop class hardware you can run it on since they don’t officially support running ESX on desktops. There are a couple of sites out there like UltimateWhiteBox.com that list various components that people have reported success in using, but obviously there is a huge range of possible hardware combinations out there on home machines, so a lot is not covered. The other issue is that it seems that the sites aren’t updated that often, if at all anymore.
Continuing my research, I looked into what processors were compatibile with ESXi 4 and settled on the Intel Quad Core. I specifically wanted a quad core processor since I was going to have several virtual machines running on it and didn’t want the processors pinned at 100% utilization from having too little cpu. I also wanted a lot of RAM for the same reason.
I was debating whether to buy all the components and build the machine myself, but every time I started pricing out components, I realized it would cost me the same or more than just buying an off the shelf desktop pc plus all the time involved in building it.
I ultimately settled on buying an HP Pavilion with an Intel Core i7 and 8gb of RAM. This would be a very solid machine at a decent price. I headed over toAmazon.com to see what they had since I could get it tax free and with free shipping.
THE BUILD
The machine arrived and I was impressed with the look. It looked like it was made to be a server with smooth glossy paint and even a cool arctic blue glowing power button. I gleefully started out trying to install ESX. First I tried ESX 3.5 and that failed since it couldn’t find my SATA controller. Next I tried ESXi 3.5 with the same result. I was getting worried but crossed my fingers and installed ESXi 4.0 and it worked! The only hiccup was that it couldn’t see the onboard network controller, which I knew would probably happen as VMware generally only recognized broadcom and Intel based NICs and the HP came with an onboard Realtek NIC.
I was bummed that I wouldn’t get to start playing immediately but was still happy that it was going to work. I headed back over to Amazon and picked up an Intel Gigabit Ct Desktop adapter for about thirty bucks. Two days later it showed up and I popped it into the machine. *Presto!* I have a fully functioning ESXi 4 VSphere server! **YAY!!**
After creating a couple of test VM’s and contemplating what type of home virtual universe I should start building, it occurred to me that the single drive in the Pavilion was not going to be big enough. I then started having my usual internal debate where my geek side fights with my cheap side over whether to buy larger drives or cheaper drives. I found a good compromise in the $119 Western Digital 2TB Caviar Green hard drives. They have an outstanding amount of storage and variable speed which allows them to spin down to a slower speed during the day while I’m away but ramp back up to full speed when I’m banging away on them doing Windows 2008 server installs.
I bought two of the drives and in another two days they arrived. I popped them in (replacing the original drive that came with the Pavilion) and reinstalled ESXi 4. Luckily the VMware installation is only about 15 minutes total. The drives worked like a charm out of the box and are drop dead silent which made me happy since I hate having the jet engine like whir of multiple hard drives in the background while I try to work.
THE RESULT
I am happy to report that over a month later, this machine is rock solid. I have two workstation VM’s and two server VM’s running 24 x 7 on it and haven’t had a hiccup. I’ve retired the hardware that my Windows Home Server was on as I’ve successfully virtualized it. I’ve found so many cool uses for it that I hadn’t even thought of before. For example, I loaded up a generic Windows XP vm that I remote control from my Apple iPad over wifi. I have another that I use when I am downloading from suspicious websites that may contain malware. When I’m done with the download and have scanned it for viruses, etc, I just power off the vm and restore it from a pristine image.
I can’t say enough about how happy this setup has made me (I know, I know, super geek)!
WHAT YOU’LL NEED
Here’s my final shopping list for this setup:
- HP Pavilion with an Intel Core i7 and 8gb of RAM
- Intel Gigabit Ct Desktop adapter
- Western Digital 2TB Caviar Green hard drives
Let me know if you’ve had success with a similar configuration or have questions about setting up your own by leaving a comment below.